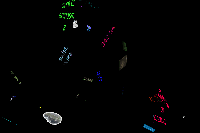A computer can be seen as an instrument on which many types and layers of writings have occurred. For example, many of us think of writing text on the computer, corresponding with friends or conducting business; we also inscribe multiple versions of a file. When a file is deleted from the hard drive – un-written, in a way – it is not immediately destroyed. Only the literal link to the file is deleted, and perhaps our awareness of the file is also lost; the actual data, however, remains in its proper block and sector until written over with new data. Even then, some fragments exist in between the written-over bits. New files mix with the layers of old, unwanted data. Thus the computer is a storehouse of artifacts: fragmented, coveted, corrupt, or precious; it holds diverse layers beneath its seamless, trustworthy user interface.
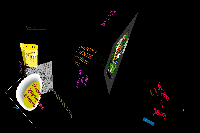
The computer is more than a diary; in a technology-infused culture it records the bulk of a person or groups of person’s work and becomes a witness and recorder of that work. If we manipulate the data inside the computer as a space, we can expose the computer as our virtual palimpsest on which more than one text has been “written” with the earlier writing incompletely erased; the place where the residues and actions of our lives are kept, partly recorded, erased. What kinds of language other than the technical can we use to describe this area so elusive to cultural and artistic study? One approach is to use the metaphor of poetics to tap into a humanistic way of thinking about data which has both inherent organizing principles.
The theory and practice of poetry, namely the area of poetics, is concerned with such fundamental questions as what poetry is, how it is read, and how it is composed and “written.” This project concerns the poetics of the computer—how form is transmutable, how tasks are multiple and fluid, and how the machine’s design and use establishes its own brand of poetics in its writing of files: order, of space, and of power. Thinking deeper into the architecture of the computer itself will allow us to consider the structure of the computer using the mechanism of a computer virus. My goals are to establish a poetics of and for the computer workstation in order to examine the user’s relation to this poetic system.
Following on mainstream attraction and revulsion of the sort of human-created life-forms that Mary Shelley brought forth in Frankenstein, the popular media’s obsession with flesh-eating contagion such as the ebola virus, or the widespread danger of HIV, viruses have developed into an important component of fiction, urban legends, hoaxes, popular media, and lawsuits. Etymologically speaking, “virus,” from the Latin virus, means, “poison.” The politics of computing are at a fevered pitch as struggles over personal identity and privacy issues peak. We are engulfed in a culmination of complex obsessions founded on the fear of the computer: as our confidant, we have a wary trust, knowing our machine can turn on us, selling our browsing habits or address books. Friend, diary, tattler, perhaps even malevolent agent…. At the pinnacle of this fear lies the computer virus.
Computer viruses have played an important role in the development of this climate through their uncanny body metaphor. The word “virus” immediately conjures up a biological equivalent for the phenomenon of computer viruses (Louw & Duffy, 1992:34). Much of their popularity seems to be based in one of two camps: one which fears for the self or host and the other which roots enthusiastically for the interruption or destruction of cyber-smooth workings of mega-national companies. Attached to a deep-seated biological analogy, computer viruses replicate by attaching themselves to a host (a program or computer instead of a biological cell) and co-opt the host’s resources to continue existence. Behaviorally, viruses are executable, self-sustaining programs; they effect or change data; and they replicate.
Why are computer viruses so frightening? Viruses place us in a periphery between the natural, organic virus and the unnatural virus of the machine; between the unintentional “natural” causes of viruses to the malevolent and intentional, between ideas of the uncontrolled and the controlled. These opposites balance in a constant state of tension in virus discourse. As contagion, viruses erase our data. But further, they invade and destroy proof: proof that we have worked, proof that we have been entertained, proof that we have remembered a history. Computer viruses recall such a profound fear because they cause users to face the fear of impermanence; along with our data our memory, experiences, the proof of our existence in our technoculture can be irretrievably destroyed.
A virus, by form or function, is not inherently harmful (Fites et al, 1992:7). Humans live with several strains of viruses in the body without consequence. Like their biological counterpart, computer viruses do not need to be destructive. Biology in fact presents us with a constructive virus type: bacteriophages, types of viruses used for healing, destroy bacteria but do not harm the human body (Intro 1996). Since the early 1900s, the capital of the Republic of Georgia, T’blisi, has been the center of phage research. Georgians use phage tablets, medications, and creams to combat illness. Phages developed at T’blisi can treat illnesses to which modern antibiotics have become immune.
A digital equivalent to this “constructive virus” can be created. To determine how we can come to an understanding of our relationship to our data, we need to not only examine its content but the technical framework which creates and stores it. One way to do this is through utilizing the imaginary of this discourse to explore the material of the system to show us something unexpected. In response to the positive image of the bacteriophage in the wake of contagion fears brought by computer viruses, I created the program [phage], with Chris Egert as technical director. [phage] is an application with viral behaviors which explores a workstation’s architecture and creates a poetics of the computer as an autonomous object, with host data as material for creative fodder. [phage], referring to the constructive bacteriophage, from the Greek phagein, meaning “to eat.”
Like biological viruses, [phage] exist in two distinct states. When not in contact with a host cell (or computer), the virus remains dormant in a non-living state. When the application comes into contact with the appropriate host, it activates. Biological viruses cannot “live” or reproduce without getting inside some living cell, nor can the computer virus [phage] exist without a host hard drive. When [phage] is ready to act, it opens, filters through all available material on a specified workstation, and visualizes it in a 3D space. [phage] places a user’s experiences in an alternate context—a visible, audible, moving 3D computer world, where the rules of what is shown, for how long, and why are created by the virus itself instead of the user.
The material conditions for creating virtual space – computer hardware and software – need to be taken into account when examining our relationship to it. Let us examine the “space” of the machine in two parts: one as a social construction of space, and one as a technically created space. The social space of the computer is a personal one, a private space which presupposes a certain intimate relationship with the user. Of course, this calls up a wider discourse about spatial structuring and social interaction and public/private spaces. These external/internal practices are deeply rooted in cultural ideologies, architectures, law, and popular discourse, subject to cultural interpretations–interpretations embedded inside a cultural reading, in our case, a technocultural reading. Here, the work of feminist geography is particularly useful in the study of the separation between public and private. Geographer Nancy Duncan see instances of privatized public space (the gated community, the shopping mall) as institutionalized, accepted, apolitical spaces by their very virtue of being fundamentally private (1996:128). With technology, this could be equated with members-only chat rooms or member shopping sites. More recently, the reverse has happened — publicized private space has developed and grown in various forms. Family/nude/gay web cams in the home, email (which is actually public communication masked as private), web browsing monitors in the workplace, and street video surveillance can be seen as sites which destabilize the assumptions of what acts or information are private.1
Because [phage] explores data in a visual display, it models and exposes the representation of the private relationship with the computer to the public—even if no one serves as spectator to these experiences “going public.” As privacy occupies a position considered “a-political” and infused with ideologies of control and intimacy, the very act of allowing the computer control over the experience creates, like a surveillance act, a blurred site for exploration.
We now need examine how the space is technically created. The hard drive could be conceptualized very much like a physical space. Or, perhaps, it could be considered like one of the virtual 3D worlds created by artists or the entertainment industry. Instead of XYZ planes, however, hard drives are gridded into divisions called sectors and can be mapped, explored, and imagined. Like an Alphaworld, Onlive! Traveller, VRML performance, or a 3D action game like Tomb Raider or Unreal, the “space” of the hard drive can be mapped, explored, and imagined. What happens when one types a text document or creates a graphic and saves it? The operating system chooses an appropriate sector of the hard drive on which to write the data. Unlike the typical 3D game experience, the maneuverings inside the “world” of the hard drive are supposed to be entirely masked to the user.
One cannot seem to avoid using metaphors of space to describe computer products or activities. Even the term “cyberspace” renders an absolute connection, associating space with the way we conceptualize information. Programming languages also suggest specialization as an operating mode within code. For example, we ask in the Basic language for the computer to “run,”(not process) and commands such as “goto” and “get” or, in Lingo, “put” or “place” (rather than compute, display, or calculate input). Such descriptions using the language of geography must be carefully considered given linguistic ties to a historic use of geography as a site of male power. 2 And more broadly, in daily life as well as in feminist discourse, there has been an adoption of such spatial metaphors in language such as “working at the margins” at the “site” of one, singular point, and suggesting that “recentering” is a way to critique status quo tropes – these refer to space as a place for strategic and political action.3
A related question to the discussion of space and meaning is: “Do 3D worlds alter the relationship between the body and knowledge?” 3D modeling and animation applications and the images they create are useful for a variety of purposes. They can be used to model difficult to understand scientific principles, such as chemical reactions or the workings of jet propulsion. Three-dimensional models and animations – human-made virtual objects – can be used as “proof” in legal cases (eg. modeling a car accident to prove that the engineering of a road is misaligned) or provide “proof of concept” in architecture. Through the simultaneity and variety of perspectives, the software packages used to create virtual worlds and characters evoke complete and total omniscience. Indeed, this “design from nowhere” aspect is prevalent not only in 3D games but in the broader scope of information technology (Suchman, 1994)4
Women in the sciences and in the arts investigate space in different ways using categories that may vary from the traditions in their fields. Women have not historically been privileged to define fields such as geography or architecture; and second, women have not been the primary designers of the computational architecture of virtual spaces. Yet the construction of virtual environments is coded in ways which strongly affect the creation of knowledge in these environments. Virtual environments are mathematically based cohesive, seamless systems which create the sense a unified order of knowledge. The construction of 3D spaces reincapsulates traditional epistemologic tropes of reason and objectivity by being abstract, outside of the body or encapsulating the virtual body. Graphics in three dimensions are meant to provide objectivity and omniscience. If, therefore, graphics in cyberspace set up this relationship of objectivity and omniscience, we as users assume this relationship unquestioningly in our complicity to user the systems we use.
The role of the body in relation to human viruses and computer viruses cannot be overlooked. The body serves as a referent to ideas not only of control but of knowledge as well. The body not only represents a cultural force but has also regulated men’s and women’s relationship to knowledge. This relationship to knowledge has a particular importance when using the computer to manifest 3D space. When we use the materials of a given episemologic condition but remove the important element of control to remap, reprioritize and display the computer architecture, we are able to find a gap in which rethink underlying power and information structures on the very machines we record our memories, experiences, and knowledges. Thus the virus project [phage] creates a visual, audible, and temporal metaphor for our experiences with the computer. [phage] sits at the axis of virtual space, public space, private space, and assumptions about control.
[phage] is a type of artificial life form, a computer virus, which explores a workstation’s architecture and creates a poetics of the computer. [phage] possesses its own organizational parameters for the mapping of virtual space, and thus works to reorient the user to the computer. [phage] exhibits viral behavior by scouring the drive, then manipulates and creates, or births, the data into a visible and audible 3D environment. Using [phage], participants experience the computer in an exceptional way through the architecture of the computer; it becomes a space for examining digital cultural creation and the structures behind the myths of digital space and identity. [phage] has only the lifespan of a computer application: it can run for days or months, or it could crash quickly. Much depends on what it discovers on the hard drive.
Let us return to the question of space. Why is it important that we think of the hard drive as a space, and how does spatialized thinking have significance? If we see the computer as a palimpsest, we can give control over these layers to the creative force of the virus. [phage] breaks down virtual space’s hierarchy by displaying information in a differently organized 3D space, granting random and many times unknown pieces of data trajectories, lifetimes, and the power of random movement. The computer in this context acts as its own creator and its own enactor of memory. Like University of California at San Diego Art professor Harold Cohen’s computer program Aaron, which uses artificial intelligence to create drawings and paintings, [phage] exhibits a large degree of autonomy in its selection and display of media on the computer.5 In other words, it is a recorder and a creator as well by re-creating our experience on the computer with different rules. [phage] functions similar to video art or other critical media works which use the medium and format to call a critique on itself. It calls a geographic critique of virtual space.
The body metaphor is intentionally significant in this project. More than simply an equative function between computer and human viruses, the body represents a significant location in power struggles and meaning in gendered terms. [phage] seeks to manifest an Irigarayian critique and counteract traditionally masculine paradigms of the technological age. In effect, the work could be thought of as an extension of Irigaray’s work. She asserts that masculinist hierarchies regulate language and material relationships, especially in regard to the body. Computers, like the body, are permeable, and this permeability is dangerous as it allows contagion as well as content to enter; the contagion, like physical or computer viruses, might consume our histories and our knowledges. Irigaray notes that the human body, with its essential need for penetration, is not easily regulated in conventional masculinist power paradigms; this permeability must be controlled through the objectification of the machine. Permeation without consent (hackers and viruses representing this danger) threatens the historic use of the computer in a command-control relationship inherited from military uses. This relationship is reinforced through the fear of the uncontrolled – viruses and hackers in fact work to validate and fortify power metaphors in computer culture. But for another type of structure to “be,” for women in cyberculture to have authorship and subjectivity, power paradigms must be altered, questioned, and reworked.
Through its inherent critical approach to a user’s relationship with the computer, the creation and organization of [phage] can counteract traditionally masculine paradigms of the technological age.Sandra Harding points out, ‘All scientific knowledge is always in every respect, socially situated’ (Harding, 1991: 11) The knowledge on which virtual space is created is based on modernist epistemology: a masculinist valued rationality upon which Western assumptions of hierarchy from Enlightenment to the present are based. Through its non-hierarchical organization and its divorce of creative control from the user to the machine, [phage] is an attempt to alter this epistemology by creating a feminist map of the machine. By allowing our communications and artifacts to be both the means and the ends of the work, [phage] allows us to become aware of our relationship with the computer, enter into the machine’s design, and examine its own brand of poetics in its writing of files, of order, and of space. Most software and art projects tell stories or provide experiences, but few are about the viewer or user. With [phage], the story is about you, the user, but told to you in a meaningful play of subjectivities.
In this case, our environment contains our own artifacts, separated from our own ordering power. [phage] allows the user to experience his or her computer memory as a palimpsest of life experiences rather than experience the computer as simply a tool for daily use. By mapping a user’s unique encounters—through images, downloads, web sites visited, emails—it creates spatial memory maps that not only reflect the user’s interactions, but to a larger degree the user’s redefinition of self within in technoculture.
Next steps? We need to encourage this virus to spread via email and establish itself (but only by the consent of the host). In a few months, material dredged up in [phage] will be sent to a server site and become part of a collective computational unconsciousness.
Endnotes
1. The Ramos Cam, Crosby FamilyCam, Jennycam, Jockcam, etc.
2. For a thorough explanation see Pratt (1992).
3. This is in reference to the argument that many concepts, at least in English speaking worlds, are associated with languages of geography and spatial metaphors (G. Lakoff & M. Johnson (1980) ).
4. Suchman is also noted in Alison Adams’ smart contribution to the study of gender and computing (Artificial Knowing (1980) ).
5. See Cohen’s work at sites such as http://www.personal.kent.edu/~brosmait/aaron.html; http://www.techreview.com/articles/may95/Holtzman.html; the book Aaron’s Code: Meta-Art, Artificial Intelligence, and the Work of Harold Cohen, by Pamela McCorduck, W. H. Freeman and Company, 1991.
References
Duncan, N. (1996) ‘Sexuality in Public and Private Spaces’, pp. 127-145 in Nancy Duncan (ed.) Bodyspace. New York: Routledge.
Fites, P, Johnston, P. & Kratz, M. (1992) The Computer Virus Crisis. New York: Wan Nostrand Reinhold.
Harding, S. (1991) Whose Science? Whose Knowledge? Ithaca, NY: Cornell University Press.Introduction to the T4 Bacteriophage. 1996. http://www.dform.com/projects/t4/virus.html
Lakoff, G. & Johnson, M. (1980) Metaphors We Live By. Chicago: University of Chicago Press.
Louw, E, & Duffy, N. (1992) Managing Computer Viruses. Oxford: Oxford University Press.
Pratt, G. (1992) ‘Spatial Metaphors and Speaking Positions’, Environment and Planning D. Society and Space. 10: 241-244
Suchman, L. (1994) ‘Working Relations of Technology Production and Use.’ Computer-Supported Cooperative Work (CSCW) 2: 21-39